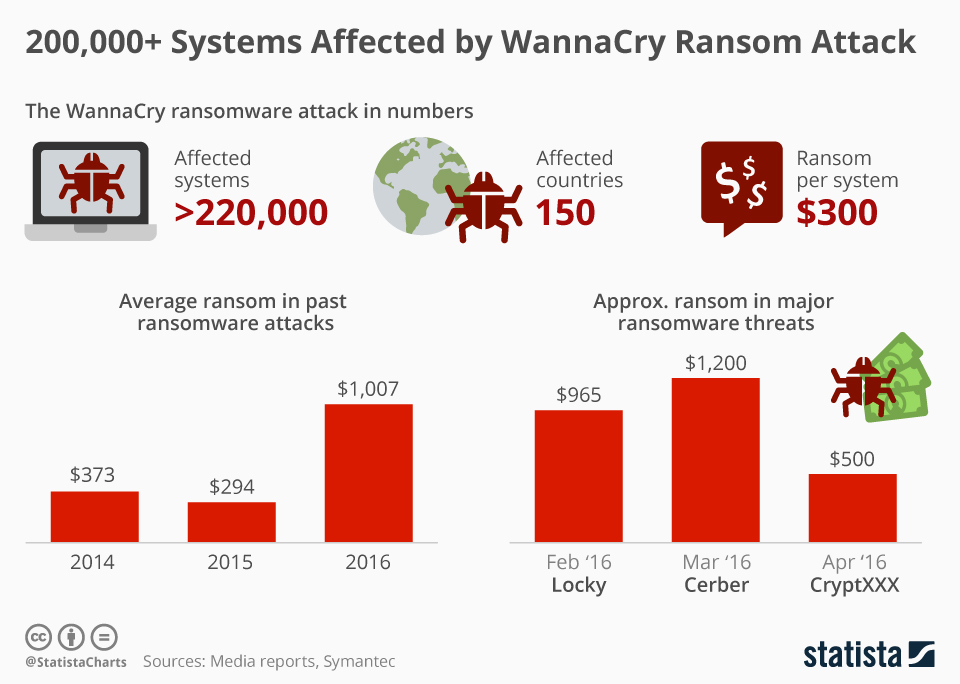
WannaCry vulnerabilities continue to pose a significant threat to modern IT security, even years after the infamous ransomware attack that exploited them. A recent report emphasizes that 67% of organizations still use insecure protocols, particularly highlighting the infamous SMBv1 vulnerabilities that fueled the widespread havoc caused by WannaCry. As businesses navigate the complexities of securing their networks, the need for effective network detection becomes paramount to protect against ransomware attacks that take advantage of these weaknesses. The report also points out that many environments still rely on other insecure protocols, raising alarm bells for IT professionals striving to bolster their defenses. It’s clear that neglecting these vulnerabilities compromises overall cybersecurity, making it essential for organizations to reevaluate their use of outdated technologies and implement sound IT practices to safeguard their operations.
The persistent issues surrounding WannaCry vulnerabilities extend beyond mere system flaws; they encompass a wider issue of legacy security protocols still utilized in various corporate infrastructures. These exploitable gaps in security, significantly represented by outdated systems like SMBv1, showcase the challenges many enterprises face in adapting to contemporary security demands. As IT teams grapple with these obsolete mechanisms, the potential for ransomware attacks looms large, underscoring the need for robust detection and mitigation strategies. Identifying insecure protocols and understanding their implications is crucial for managing risk and preventing future breaches. Therefore, organizations must comprehensively audit their networks to enhance their resilience against evolving cyber threats.
Understanding WannaCry Vulnerabilities Today
Despite the passage of several years since the infamous WannaCry ransomware attack, a staggering number of IT environments are still vulnerable. The ExtraHop report reveals that a vast majority, around 67%, of organizations continue to use insecure protocols such as SMBv1, which were directly exploited during the WannaCry incident. This persistence highlights a critical gap in IT security, revealing that even with increased awareness of threats, many enterprises have not taken action to update or replace outdated systems.
The vulnerabilities associated with WannaCry are not just relics of past attacks but continue to pose a real threat to networks today. Organizations that fail to address these weaknesses risk becoming targets for similar ransomware attacks. The complexity of phasing out legacy protocols, coupled with the operational challenges involved, means that many firms are caught in a cycle of maintaining lifelines to unsafe technologies, thereby exposing themselves to further risks.
The Impact of SMBv1 Vulnerabilities in Modern IT
SMBv1 vulnerabilities have become a critical focal point for IT security teams as they strive to fortify defenses against emerging threats. The aged protocol, which has been the backbone of file sharing in Windows environments since the 1980s, is notorious for its susceptibility to attacks. The recent findings from ExtraHop underscore that 67% of environments still harbor this protocol, making them easy targets for potential intruders utilizing ransomware like WannaCry.
Transitioning away from SMBv1 is essential for organizations to strengthen their IT security. However, the challenge lies in the need for a careful assessment of operational dependencies tied to this protocol. Many businesses are reluctant to make abrupt changes that could lead to service disruptions, thus complicating the task of eliminating these vulnerabilities. Consequently, IT departments must prioritize creating a solid inventory of their assets to adequately understand and address risks associated with outdated protocols, including SMBv1.
The Role of Insecure Protocols in Network Security
Insecure protocols remain a pervasive element in many enterprise environments, posing significant threats to network security. The continued use of protocols like LLMNR, NTLMv1, and HTTP highlights a widespread issue where organizations fail to adapt to newer, more secure alternatives. The ExtraHop report indicates that up to 81% of enterprise environments still utilize plain text credentials over HTTP, reflecting a lack of awareness or urgency around effective IT security measures.
The risks posed by these insecure protocols extend beyond mere data breaches; they open the door for advanced ransomware attacks that can cripple organizational functionality. Proper network detection mechanisms should be implemented to identify and mitigate the use of such protocols. Organizations must prioritize securing their networks against easily exploitable vulnerabilities by enforcing policies that phase out insecure methods and adopting more secure alternatives.
Addressing Legacy Systems and Their Risks
One of the most pressing challenges in modern IT security is managing legacy systems that rely on outdated protocols. As organizations strive to secure their networks, they often face pushback when it comes to transitioning away from long-standing systems that incorporate insecure protocols like SMBv1. This dependency complicates efforts to address security vulnerabilities, as businesses worry about potential downtime and the impact on operational continuity.
Nevertheless, organizations must find a balance between maintaining critical legacy systems and improving their security posture. This may include implementing layered security measures, such as network segmentation and continuous monitoring, to mitigate risk exposure while still utilizing legacy applications. Ultimately, addressing the risks of legacy systems requires a strategic approach that involves assessing the specific vulnerabilities present and prioritizing them for remediation.
Importance of Comprehensive Asset Inventory
A fundamental component of securing IT environments is the creation of a comprehensive asset inventory. This inventory allows organizations to have a clear understanding of what assets they possess, how they’re utilized, and what vulnerabilities they may hold. The ExtraHop report emphasizes that organizations often lack this crucial knowledge, which is vital in evaluating their risk posture regarding insecure protocols and potential attacks.
By conducting thorough asset inventories, organizations can accurately identify outdated protocols that are in use, such as SMBv1 and NTLMv1. This understanding enables security teams to focus their efforts on eliminating vulnerabilities that pose the highest risks. Moreover, a real-time view of network activity helps in proactively managing potential threats, ensuring maximum protection against ransomware attacks and other forms of cyber threats.
Mitigating Ransomware Attacks with Strong IT Security
To effectively mitigate the risk of ransomware attacks, organizations must establish strong IT security protocols that go beyond mere compliance with standards. As indicated by the continued prevalence of insecure protocols in IT environments, many organizations are still vulnerable to these threats. A robust security posture involves not just implementing new technologies, but also actively phasing out legacy systems that utilize outdated protocols.
Mitigation efforts should also that include regular security audits and employee training on recognizing and responding to ransomware threats. By fostering a culture of security awareness, organizations can enhance their defenses and reduce the likelihood of a successful attack. Furthermore, employing advanced network detection and response solutions can assist in identifying vulnerabilities before they are exploited, thereby fortifying organizational security.
The Need for Security Protocol Evolution
The evolution of security protocols in response to emerging threats is vital in today’s cybersecurity landscape. Technologies such as SMBv1 have been outpaced by more secure alternatives, yet their continued use speaks to a broader issue within the industry. Organizations may prioritize short-term operational needs over long-term security, leading to an enduring cycle of vulnerability that impacts their resilience against attacks.
Evolving security protocols should be a proactive initiative taken by organizations, aligning with the latest security practices and guidelines. The switch to more secure protocols can help contain risks and prevent potential ransomware attacks. Furthermore, as organizations become more aligned with best practices, they can better engage in strategic conversations about their security posture, encouraging an environment of continuous improvement within their IT frameworks.
Strategic Risk Management in IT Security
Effective risk management strategies are essential for modern IT security. Organizations need to assess their current security landscape and identify potential weaknesses that could be exploited by ransomware or other cyber threats. By aligning risk management efforts with a clearly defined understanding of vulnerabilities, particularly those associated with insecure protocols, organizations can develop targeted strategies that minimize their exposure.
Implementing an agile strategy allows organizations to adapt quickly to emerging threats while maintaining operational effectiveness. This may involve training IT staff to manage risk assessments diligently, ensuring they can eliminate vulnerabilities like SMBv1 from their networks. Through strategic risk management, companies can not only mitigate immediate threats but also foster a culture of security that prioritizes sustainability and resilience in the long term.
Future-Proofing IT Environments Against Cyber Threats
Looking forward, organizations must adopt progressive measures to future-proof their IT environments against evolving cyber threats, including ransomware attacks. This involves not only upgrading outdated protocols, such as SMBv1, but also staying informed about the latest advancements in cybersecurity technology and practices. Emphasizing a proactive stance can significantly diminish the risk of vulnerabilities being exploited by attackers.
Organizations can future-proof their IT environments by investing in modern infrastructure and adopting best practices related to cybersecurity. Continuous monitoring and regular vulnerability assessments can play a substantial role in identifying weak points before they lead to successful cyber-attacks. By fostering a culture where IT security is prioritized, businesses can protect themselves against not only WannaCry but also any future threats that might emerge.
Frequently Asked Questions
What are the main WannaCry vulnerabilities affecting IT security today?
The primary WannaCry vulnerabilities include the exploitation of SMBv1 (Server Message Block version one), which remains prevalent in many IT environments. This outdated protocol enabled WannaCry ransomware to encrypt hundreds of thousands of machines globally. Organizations that continue to use insecure protocols like SMBv1 are at significant risk of ransomware attacks.
Why is SMBv1 a significant vulnerability associated with WannaCry?
SMBv1 is a major WannaCry vulnerability due to its outdated nature and security flaws that attackers exploit. This protocol was responsible for the rapid spread of the WannaCry ransomware, resulting in thousands of infected systems. Many enterprises still use SMBv1, making it critical for IT security teams to prioritize its replacement.
How can network detection help mitigate WannaCry vulnerabilities?
Network detection is vital in identifying WannaCry vulnerabilities like SMBv1. By monitoring network traffic, organizations can detect insecure protocols and unauthorized activities indicative of ransomware attacks. Implementing effective network detection strategies allows IT security teams to respond promptly and reduce potential risks.
What percentage of environments are still vulnerable to SMBv1 exploitation?
According to recent reports, approximately 67 percent of IT environments still utilize SMBv1, leaving them vulnerable to exploitation by ransomware like WannaCry. This underscores the importance of addressing these insecure protocols to improve overall network security.
What challenges do organizations face when transitioning from SMBv1 to secure protocols?
Organizations encounter significant challenges when moving away from SMBv1, including potential service disruptions and compatibility issues with legacy systems. Many IT and security teams opt to contain the use of outdated protocols instead of undertaking risky migrations. A thorough evaluation of asset behavior is essential to navigate these challenges effectively.
How do insecure protocols lead to increased risk of ransomware attacks?
Insecure protocols such as SMBv1, LLMNR, and NTLMv1 pose substantial risks by providing attack vectors for ransomware like WannaCry. These vulnerabilities create opportunities for cybercriminals to exploit, infiltrate, and ultimately compromise sensitive data across IT environments, increasing the likelihood of ransomware attacks.
What should organizations do to address WannaCry vulnerabilities effectively?
To effectively manage WannaCry vulnerabilities, organizations should conduct a detailed inventory of their network assets and identify any insecure protocols in use. They must prioritize the transition from outdated protocols like SMBv1, considering both risk assessment and potential service impacts, while also employing network detection tools to monitor for threats.
| Key Point | Details |
|---|---|
| WannaCry Attack Anniversary | A new report highlights that a significant percentage of IT environments still operate with known vulnerabilities on the fourth anniversary of the WannaCry attack. |
| Insecure Protocols | The report indicates persistent use of insecure protocols like SMBv1, exploited by WannaCry, and still present in 67% of environments. |
| LLMNR and NTLMv1 Usage | 70% of environments continue using LLMNR and 34% have at least 10 clients using NTLMv1. |
| HTTP Credentials | 81% of enterprises still utilize insecure HTTP plain text credentials. |
| Challenges of Migration | Transitioning away from outdated protocols like SMBv1 can cause service disruptions, making it complex for organizations. |
| Need for Inventory | Organizations must have a precise and current inventory of their assets to properly assess risks related to insecure protocols. |
Summary
WannaCry vulnerabilities continue to pose a significant risk to IT environments as recent reports highlight the ongoing prevalence of insecure protocols like SMBv1, LLMNR, and NTLMv1. Despite efforts to address these vulnerabilities post-WannaCry, many organizations are still grappling with the challenges of phasing out these outdated protocols, often opting to contain rather than eliminate them to avoid disruptions. A comprehensive asset inventory is crucial for organizations striving to improve their risk posture and secure their networks against these persistent threats.